Getting ready
For this example, you will need a web server running Oracle Linux. The server needs to be accessible over the internet so that the Let’s Encrypt system can verify the URL. In this example, I will be using a VM on Oracle Cloud, using their free tier of service. This VM is running on an Arm-based CPU with 2 cores and 12 GB RAM. Both ports 80 and 443 are opened up to this server. This process works the same regardless of processor type or cloud. The system is running Oracle Linux 8 with the latest patches.
How to do it…
To do this, we need to do a few things:
- Install Apache with mod_ssl and all its requirements.
- Get acme.sh from Git.
- Create a cert using the webroot mode. Webroot mode requires that the site is accessible from the internet on both ports 80 and 443. While it is easy to implement, there is another verification method using DNS. For more information about different challenge types, refer to https://letsencrypt.org/docs/challenge-types/.
- Conduct testing.
Installing Apache with mod_ssl and all its requirements
- So let’s get started as the root user. First, we need to add some packages:
• httpd – Apache web server
• mod_ssl – enables SSL on Apache
You can do this with the following command:
dnf install -y httpd mod_ssl
- Next, let’s add both ports 80 and 443 to the firewall. This is done as the root with the following commands:
firewall-cmd –zone=public –permanent –add-service=http
firewall-cmd –zone=public –permanent –add-service=https
firewall-cmd –reload apache
- Now, let’s set up a virtual server for ssltest.talesfromthedatacenter.com. This way, we can later add the SSL certs just for this virtual server. As the root, let’s make a directory for the files and chown them to the apache user:
mkdir -p /var/www/ssltest
chown apache:apache /var/www/ssltest
- Next, we will add a config file ssltest.conf in /etc/httpd/conf.d:
# Put this in /etc/httpd/conf.d/ssltest.conf Alias /.well-known/acme-challenge/ /var/www/ssltest/.well-known/acme-challenge/ Options None AllowOverride None ForceType text/plain RedirectMatch 404 “^(?!/.well-known/acme-challenge/[\w-]{43}$)” RewriteEngine On RewriteCond %{REQUEST_URI} !^/.well-known/acme-challenge [NC] RewriteCond %{HTTPS} off RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L]
- After you save the file, run an apachctl configtest. It is good practice to always run this test when you modify the config files.
apachectl configtest
Syntax OK
- Next, let’s start Apache and make sure we can get to the default page. The enable option will restart the web server when the system starts. The –now option will start the server now:
systemctl enable –now httpd
- Now, point your browser to the site on port 80. You should see the default Apache page. Notice, the Not secure flag in the upper-left corner! The site is not using SSL:
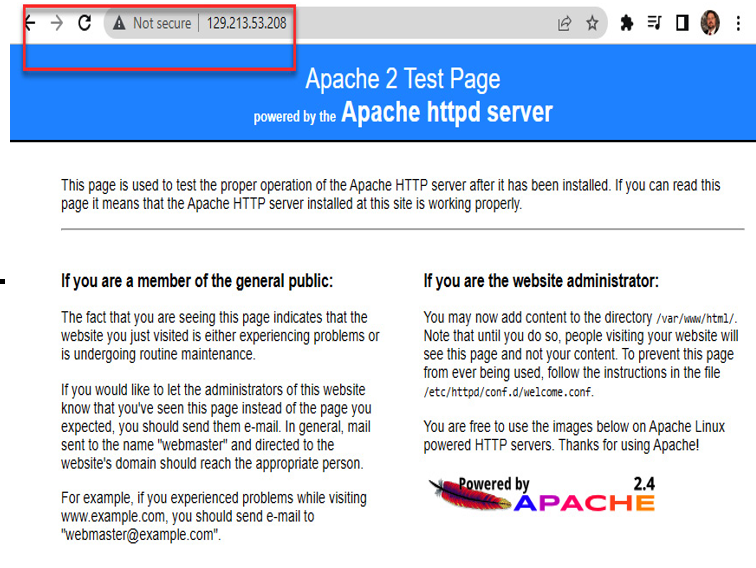
Figure 9.3 – Apache test page with no SSL